
Let’s Encrypt is one of the few services that give you free SSL certificates, valid for 30 days, a great solution to protect your website.
I’ve been using Certbot for a while to manage my certificates with NGINX, and I’ve never been so satisfied by using a free service like this one.
TLS-SNI-01 is now obsolete and considered highly insecure
Certbot renews certificates with an old encryption algorithm, the infamous TLS-SNI-01, which is no longer used by Let’s Encrypt to generate certificates. But why?
The security professional Frans Rosén has discovered a harmful bug that gives to hackers the power to hijack certificates and exploit entire infrastructures to get certificates that you do not even own.
Still interested about the bug? Read here
Despite the fact that so far no one ever abused of any certificate on Let’s Encrypt, the service discontinued the support to TLS-SNI-01 inviting every user to disable that kind of protocol on Certbot in favor of different ones.

Check your email for updates from Let’s Encrypt
So, at the beginning of the new year I received an email from Let’s Encrypt that warned me to disable TLS-SNI-01 manually on Certbot in order to not break the continuity service. In fact, older versions of Certbot are still using the old TLS to renew SSL despite of the fact that in a short amount of time it’s going to be finally unsupported.
This is the email I received:
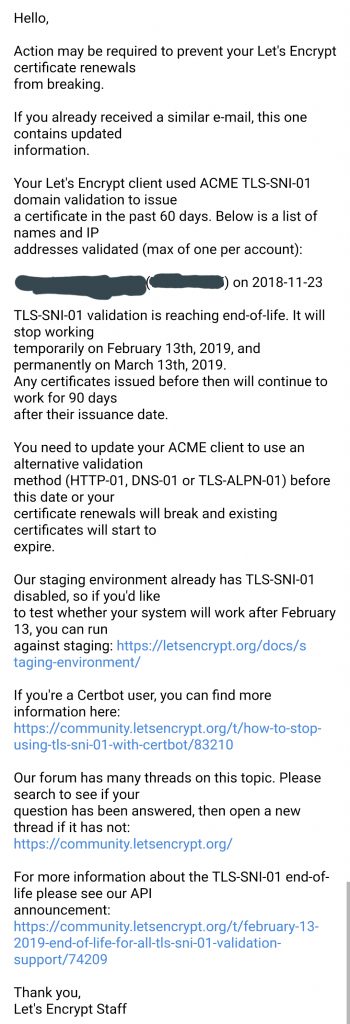
How to permanently disable TLS-SNI-01
Then, how do we disable it in order to prevent our services from being insecure?
Luckily for you, the process is really straightforward and it doesn’t take a lot of time. Obviously, the more domains you have the more time it’s going to take.
The following method has been tested by me on a server using CentoOS 7 though there shouldn’t be any problem at all to disable it on your machine.
First things first. Please issue the following command to your terminal to see the version of the Certbot client that you are currently using:
certbot --version || /path/to/certbot-auto --version
The required version in order to make it work is
Now, all we have to do is to remove all the references to the acme tls-sni-01 from the client by simply invoking this command:
sudo sh -c "sed -i.bak -e 's/^\(pref_challs.*\)tls-sni-01\(.*\)/\1http-01\2/g' /etc/letsencrypt/renewal/*; rm -f /etc/letsencrypt/renewal/*.bak"
That’s it! Well, almost… the final required command is to force Certbot to update all the existing certificates and ask to build them using a different protocol.
sudo certbot renew --dry-run
You might have to wait some more minutes in order to be good to go, but if nothing has failed, you solved the problem.

I hope that this short guide was helpful for you. If it didn’t solve the problem you might ask help on the official Let’s Encrypt forum on this page.

